Sophos Email Guide: Secure Your Communications in 2026
Secure your business email in 2026 with our expert Sophos Email guide. Discover advanced protection strategies, deployment steps, and best practices for robust security.
Email remains the backbone of business communication, but in 2026, attackers are more cunning and persistent than ever. Recent reports show that 90% of security breaches now originate from email, making strong protection a necessity.
This guide delivers a complete roadmap to defend your organization using sophos email. You will discover the latest security challenges, advanced features, step-by-step deployment, integration tips, best practices, and real-world success stories.
Ready to secure your communications and outsmart evolving threats? Let’s dive in.
The Evolving Landscape of Email Threats in 2026
Email security in 2026 faces unprecedented challenges. Attackers are more organized, their methods are smarter, and the stakes for businesses have never been higher. Organizations must understand how the threat landscape has evolved to effectively deploy sophos email as a frontline defense.

Rise of Phishing, BEC, and Ransomware Attacks
Phishing continues to dominate as the leading attack vector. Industry reports confirm that 90% of breaches now originate from malicious emails. Business Email Compromise (BEC) has become more costly, with global losses predicted to exceed $3 billion this year.
Ransomware attacks delivered through email attachments have surged, increasing by 30% year-over-year. High-profile incidents, such as breaches in the financial and healthcare sectors, highlight how quickly attackers exploit vulnerabilities. These trends underscore the critical importance of implementing sophos email to block these threats before they reach end users.
Sophos email is essential for organizations seeking to safeguard sensitive data and maintain operational continuity in this hostile environment.
Sophistication of Attack Techniques
Attackers have adapted quickly, leveraging AI to craft phishing emails that bypass traditional filters and fool even vigilant recipients. The use of deepfake technology and voice phishing (vishing) is on the rise, making it harder for employees to distinguish genuine communications from fraudulent ones.
Social engineering attacks now target remote and hybrid workers, exploiting their reliance on digital communication. Credential harvesting tactics have grown more advanced, often using fake login pages that appear legitimate. According to recent reports, AI enhances phishing email effectiveness, making the need for sophisticated detection tools like sophos email more urgent than ever.
Regulatory and Compliance Pressures
Regulatory bodies have responded to the growing threat landscape with stricter rules. Updates to GDPR, NIS2, and HIPAA now require organizations to adopt stronger email security measures. Non-compliance can result in steep fines and severe reputational damage.
Sophos email helps businesses stay compliant by providing advanced protection and detailed reporting. Organizations must now demonstrate due diligence in protecting sensitive information shared over email, or risk significant penalties.
Challenges for Modern Organizations
Modern organizations face a unique set of challenges in securing email. The widespread adoption of cloud-based platforms like Microsoft 365 and Google Workspace has expanded the attack surface. Employees increasingly access email on mobile devices, often through BYOD policies, creating more entry points for attackers.
Many small and midsize businesses lack the IT resources to manage email security effectively. Sophos email offers a solution that addresses these challenges, providing robust protection that adapts to the evolving needs of today’s distributed workforce.
Sophos Email: Core Features and Innovations for 2026
Email threats in 2026 are more dynamic and dangerous than ever, demanding advanced defenses that keep pace. Sophos email brings a full suite of innovations to the table, blending intelligence, automation, and ease of use for organizations of all sizes. Let’s examine the core features that set sophos email apart from the competition.

Multi-Layered Threat Protection
Sophos email employs a multi-layered approach to defend against sophisticated attacks. This includes advanced anti-phishing, anti-malware, and anti-spam engines that work in tandem to block known and unknown threats. Behavioral analysis is at the core, identifying zero-day threats and evasive malware before they reach inboxes.
Real-time URL scanning and attachment sandboxing provide an extra line of defense. AI and machine learning models enable intent-based threat detection, adapting to attackers' evolving tactics. For a comprehensive look at these capabilities, see the Product Features Overview.
Business Email Compromise and Impersonation Defense
Business email compromise (BEC) is a top threat, but sophos email offers robust tools to neutralize it. Impersonation detection actively blocks CEO fraud and spoofing attempts by analyzing sender behavior and communication patterns.
Dynamic sender verification and anomaly detection help spot suspicious emails in real time. For example, a financial services firm recently thwarted a targeted BEC attack using sophos email’s advanced controls, preventing significant financial loss.
Seamless Cloud Integration
Modern organizations rely on cloud-based email platforms like Microsoft 365 and Google Workspace. Sophos email integrates natively with these services, ensuring consistent protection without disrupting workflows.
API-based integration enables real-time threat intelligence sharing, keeping defenses up to date. Centralized management through the Sophos Central platform simplifies policy administration across cloud and on-premises environments, making security both powerful and practical.
Data Protection and Encryption
Safeguarding sensitive information is essential for compliance and business continuity. Sophos email automates data loss prevention (DLP) with customizable policies that recognize and protect confidential content.
End-to-end email encryption is built in, supporting GDPR, HIPAA, and other regulatory requirements. Granular controls allow administrators to manage attachment handling and outbound email policies, reducing accidental data leaks and reinforcing trust.
Security Awareness and User Training
Human error remains a leading cause of breaches, so sophos email integrates security awareness directly into the platform. Built-in phishing simulation and user training modules test and educate employees on the latest threats.
Sophos Phish Threat, available within the suite, enables ongoing education tailored to user behavior. Comprehensive reporting tools track progress, highlight risky users, and support continuous improvement in security posture.
Award-Winning Performance
Sophos email consistently earns top marks from independent analysts and customers. It was recognized as a leader in the KuppingerCole 2025 Leadership Compass and achieved a 100% malware catch rate with zero false positives in the VBSpam Q2 2025 test.
Customer testimonials highlight improved security and peace of mind. Sophos email stands out for its reliability, precision, and ability to adapt as new threats emerge.
Step-by-Step Guide to Deploying Sophos Email
Securing your organization’s communications starts with the right deployment strategy. This section breaks down the essential steps for implementing sophos email, ensuring your team benefits from comprehensive protection from day one. Each phase below is designed to simplify setup, boost security, and align with your business needs.

Planning and Preparation
Begin by assessing your current email infrastructure. Identify any existing vulnerabilities and map out where sophos email will provide the most value.
Next, define your compliance requirements, such as GDPR or HIPAA, to ensure all legal obligations are met. Bring together key stakeholders from IT, compliance, and management to clarify objectives and assign responsibilities.
A clear plan at this stage prevents missteps and accelerates a smooth deployment. Document your findings and prepare a checklist to guide the process.
Deployment Process
Access the Sophos Central management console, which serves as the central hub for sophos email administration. Register your organization and connect sophos email to your chosen platform, whether Microsoft 365, Google Workspace, or another provider.
Follow the official Get Started with Email Protection guide for step-by-step instructions. Configure your MX records and update mail flow settings according to sophos documentation. Double-check all connections to ensure seamless mail delivery.
A successful deployment ensures that all inbound and outbound messages are filtered and protected from the outset.
Policy Configuration and Customization
With sophos email integrated, set up your security policies to match your risk profile. Enable anti-phishing, anti-malware, and spam filtering features.
Activate impersonation protection to defend against business email compromise. Configure Data Loss Prevention (DLP) rules to prevent sensitive data leaks.
Customize quarantine notifications and user alerts to keep staff informed. Granular policy controls allow you to tailor security to your organization’s unique requirements.
Testing and Validation
Before going live, validate your sophos email deployment through rigorous testing. Run simulated phishing attacks to confirm detection capabilities.
Monitor email flow and review threat detection logs for anomalies. Adjust policies based on findings, ensuring that legitimate messages are delivered and threats are blocked.
Regular validation keeps your defenses sharp and builds confidence in your email security posture.
Go-Live and Ongoing Management
Once testing is complete, roll out sophos email organization-wide. Communicate new security protocols to all users and provide training if needed.
Schedule regular policy reviews and leverage the Sophos Central dashboard for active monitoring. Update configurations as threats evolve and regulations change.
Continuous management ensures sophos email remains effective, keeping your communications secure well into the future.
Best Practices for Maximizing Email Security with Sophos
Securing your organization against advanced email threats requires more than just technology. To truly maximize the power of sophos email, it is essential to adopt a holistic approach that combines technology, user awareness, and ongoing optimization. The following best practices will help you build a resilient defense.
Layered Security Approach
A layered security strategy is the cornerstone of robust email protection. By integrating sophos email with endpoint, firewall, and identity solutions, you create multiple barriers against threats. This defense-in-depth model minimizes risk even if a single layer is bypassed.
Benefits of Layered Security:
| Layer | Purpose | Example Solution |
|---|---|---|
| Email Gateway | Blocks phishing, spam, malware | sophos email |
| Endpoint | Stops local threats | Sophos Intercept X |
| Firewall | Prevents network intrusions | Sophos Firewall |
| Identity | Secures user access | Sophos Central Identity |
For deeper insights into evolving strategies, refer to the Email Security Blog Insights, which offers expert perspectives on new threats and layered defenses.
User Training and Phishing Simulations
Even the most advanced security platform cannot compensate for untrained users. Regularly running simulated phishing campaigns through sophos email helps staff recognize suspicious messages and reduces human error.
- Launch monthly phishing simulations
- Track who clicks and tailor follow-up training
- Reinforce lessons with short, interactive modules
Continuous education ensures users remain vigilant and act as your first line of defense.
Policy Optimization and Fine-Tuning
Threats evolve, so your email policies must as well. Review sophos email threat reports and adjust filtering sensitivity based on trends. Use threat intelligence feeds to stay proactive.
Practical steps include:
- Weekly review of spam and phishing quarantine logs
- Adjust rules for new attack patterns
- Exclude business-critical domains from aggressive filtering
Fine-tuning policies maintains a balance between security and productivity.
Incident Response and Threat Remediation
A rapid response to incidents is vital for minimizing damage. sophos email enables automated workflows that detect and contain threats before they spread.
- Set up automated incident response actions in Sophos Central
- Integrate with Sophos MDR for expert guidance
- Define escalation paths for critical incidents
Having a clear plan ensures your team reacts quickly and effectively when an attack occurs.
Compliance and Audit Readiness
Regulations demand proof of robust controls. sophos email simplifies compliance by generating detailed audit logs and customizable reports to demonstrate adherence to GDPR, HIPAA, or NIS2.
- Schedule monthly compliance report generation
- Use built-in templates for regulatory frameworks
- Store logs securely for audit events
Being audit-ready reduces risk of fines and reputational harm.
Real-World Example: Sophos Email Stops Ransomware Attack
Recently, a financial services firm faced a targeted ransomware email. sophos email identified the malicious payload, quarantined the message, and alerted IT before any damage occurred.
Lessons learned:
- Regularly update detection engines
- Simulate attacks to test defenses
- Review incident logs after any event
This case highlights the importance of layered protection and vigilant monitoring.
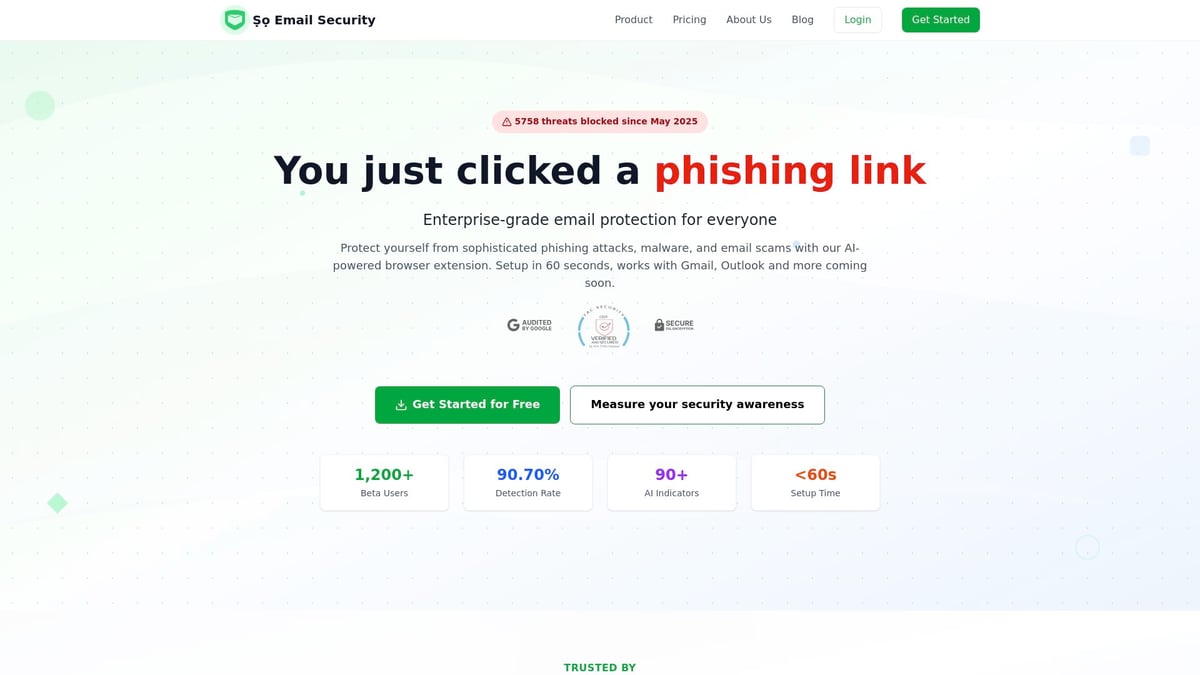
Ṣọ Email Security: AI-Powered Email Protection for Individuals and SMBs
For small businesses or individuals without dedicated IT, Ṣọ Email Security offers a free browser extension that analyzes emails in real time. With over 90 threat indicators and instant explanations, it simplifies inbox management while delivering enterprise-grade protection and privacy by design.
Integrating Sophos Email with Your Broader Security Ecosystem
Securing modern communications requires more than isolated solutions. Integrating sophos email with your broader security ecosystem brings unified defense, increased visibility, and streamlined operations. By connecting key tools and leveraging automation, organizations can transform email protection into a proactive shield.
Centralized Management with Sophos Central
Centralizing management is essential for efficient security operations. With sophos email, the Sophos Central platform provides a unified dashboard to oversee email, endpoint, firewall, and cloud security. This approach allows administrators to manage policies, monitor threats, and respond to incidents from a single pane of glass.
Streamlined management reduces complexity and minimizes gaps in protection. Automated alerts and real-time monitoring ensure that no threat slips through the cracks. Sophos Central’s intuitive interface empowers IT teams to act quickly, keeping sophos email defenses up to date.
API Integrations and Automation
Sophos email supports robust API integrations that connect with SIEM, SOAR, and third-party security tools. This connectivity enables organizations to automate incident response workflows and share threat intelligence in real time. By leveraging these integrations, teams can coordinate defenses across the entire environment.
For example, integrating sophos email with threat intelligence feeds helps identify and block new attack vectors, such as malicious URLs surpassing email attachments as top malware threat. Automation reduces manual workload, improves response times, and ensures consistent enforcement of policies.
Enhancing Visibility and Reporting
Visibility is crucial for proactive security. Sophos email delivers advanced analytics on email threats, user behavior, and attack trends. Customizable alerts and scheduled reports keep stakeholders informed, supporting timely decision-making.
By monitoring metrics such as credential theft, which surged 160% in 2025, organizations can adapt their defenses. Detailed reporting from sophos email empowers compliance, risk management, and continuous improvement.
Collaboration with Managed Security Services
For many organizations, partnering with managed security services is a strategic advantage. Sophos email integrates seamlessly with Sophos MDR, offering expert-led threat hunting and remediation. Outsourcing incident response enables rapid containment and recovery, reducing business impact.
Sophos MDR specialists work alongside in-house teams to maximize sophos email’s effectiveness. This collaboration ensures 24/7 coverage and access to the latest threat intelligence, enhancing organizational resilience.
Example: Integrating Sophos Email with Microsoft Defender
Combining sophos email with Microsoft Defender provides layered protection against sophisticated threats. This integration allows for cross-platform threat correlation, improving detection accuracy and response speed.
Organizations can synchronize alerts and coordinate policies between sophos email and Defender. The result is a robust security posture, with comprehensive coverage across email, endpoint, and cloud environments.
Future Trends: Email Security Beyond 2026
The future of email security is rapidly evolving, with organizations facing new threats and compliance challenges every year. As attackers innovate, businesses must stay ahead by embracing advanced solutions like sophos email. Understanding the trends shaping the landscape beyond 2026 is crucial for building resilient defenses.
AI and Machine Learning Advancements
Artificial intelligence is reshaping how threats are detected and blocked. By 2026, generative AI will enable predictive threat detection, allowing sophos email to identify and neutralize attacks before users ever see them. Machine learning models will adapt in real time, analyzing massive datasets to spot new phishing techniques and malware variants.
Adaptive filtering will become standard, evolving as attacker tactics shift. This means sophos email can proactively counter zero-day exploits and engineered attacks. As AI continues to mature, it will drive both the sophistication of cyberattacks and the agility of cyber defenses.
Zero Trust and Identity-Centric Security
Zero trust frameworks are set to become the norm for email access. Instead of relying solely on traditional perimeter defenses, sophos email will integrate with identity threat detection and response (ITDR) to verify every message, user, and device.
With remote work and cloud adoption increasing, identity-based controls ensure only authenticated users can access sensitive content. Continuous monitoring, multi-factor authentication, and behavior analysis will further reduce risk. By focusing on identity, sophos email will help organizations prevent lateral movement and data exfiltration through compromised accounts.
Regulatory Evolution and Compliance Demands
Global regulations are tightening, requiring organizations to elevate their email security standards. Laws like GDPR, HIPAA, and new frameworks such as NIS2 are imposing stricter controls, with heavier penalties for non-compliance. Healthcare and finance sectors, in particular, face mounting scrutiny due to high-profile breaches.
For example, recent healthcare email security vulnerabilities in Microsoft 365 highlight the urgent need for robust solutions like sophos email. Automated compliance reporting, encryption, and audit-ready logs will be essential for passing regulatory checks and safeguarding sensitive data.
Rise of Deepfake and Social Engineering Attacks
Attackers are leveraging AI to craft convincing deepfake audio, video, and text, making social engineering attacks more difficult to detect. Sophos email is evolving to recognize synthetic content by analyzing message metadata, communication patterns, and even subtle writing cues.
Training users to spot these advanced threats will remain vital. Built-in awareness modules and ongoing simulations will help employees identify suspicious messages, reducing the risk of falling victim to deepfake-driven scams. As threat actors get smarter, so will the defensive tools embedded within sophos email.
Cloud-Native and API-Driven Security Architectures
With businesses relying heavily on SaaS platforms, cloud-native security is now a requirement. Sophos email is designed for seamless integration with cloud providers, supporting API-driven automation for threat detection and response.
APIs enable real-time data sharing between sophos email and other security tools, improving visibility and accelerating incident response. The platform’s roadmap includes even deeper cloud integration, ensuring organizations can scale protection as their digital footprint grows. Future enhancements will prioritize flexibility, speed, and interoperability.
Recommendations for Staying Ahead
To proactively defend against future threats, organizations should:
- Invest in user education and ongoing security awareness.
- Regularly update sophos email policies based on threat intelligence.
- Leverage automation and AI-driven tools for rapid response.
- Partner with trusted vendors to ensure compliance and adaptability.
Staying vigilant, agile, and informed will help businesses harness the full power of sophos email and maintain a strong security posture in the years ahead.